Protecting Yourself from Scammers: Safeguarding Data Privacy in the Digital Age
In today’s interconnected world, we rely heavily on technology for various aspects of our lives, including financial transactions. However, this increased dependence on digital platforms also exposes us to potential threats, such as scammers and data breaches. Recently, I experienced firsthand the dangers of falling victim to unsolicited messages and scams, highlighting the importance of protecting our data privacy. In this blog, I aim to raise awareness and provide practical tips to help you safeguard your personal information and avoid falling prey to fraudulent schemes.
The Perils of Unsolicited Messages:
Imagine receiving messages from unknown numbers, filled with alarming claims and links that entice curiosity or fear. Unfortunately, these messages often serve as a gateway for scammers to exploit unsuspecting individuals. Such messages revealed a concerning breach of data privacy. It became evident that these scammers somehow obtained my contact details, indicating a possible connection to my recent search for financial assistance through Non-Banking Financial Companies (NBFCs).
Understanding Scammers’ Techniques:
To shed light on how scammers operate, I delved into the intricacies of their manipulative techniques. By sharing these insights, I hope to empower others with knowledge and help them avoid falling into similar traps. The following steps outline the typical progression of a scam:
Step 1: Manipulating App Ratings and Visibility:
Scammers often employ tactics to ensure their apps appear at the top of search results in app stores. By running ads and artificially boosting their ratings, they create an illusion of credibility that entices users to download the app without thoroughly scrutinizing it.
Step 2: Requesting Excessive Permissions:
During the app’s installation, scammers request permissions that seem ordinary, such as camera access, microphone access, and location access. These requests mimic those made by legitimate applications, making it challenging to distinguish malicious intent.
Step 3: Collecting Personal Information:
Similar to genuine lending apps, scam apps ask for basic personal information, including names, phone numbers, Aadhar card numbers, PAN card numbers, selfies, and emergency contacts. At this stage, nothing appears suspicious, as scammers mimic legitimate processes to gain victims’ trust.
Step 4: Exploiting Collected Data:
After obtaining victims’ information, scammers either declare them ineligible for a loan or offer small amounts with exorbitant processing fees or interest rates. Most individuals would avoid such unfavourable terms. However, scammers already possess all the necessary information to carry out their fraudulent activities.
Step 5: Unleashing Threats:
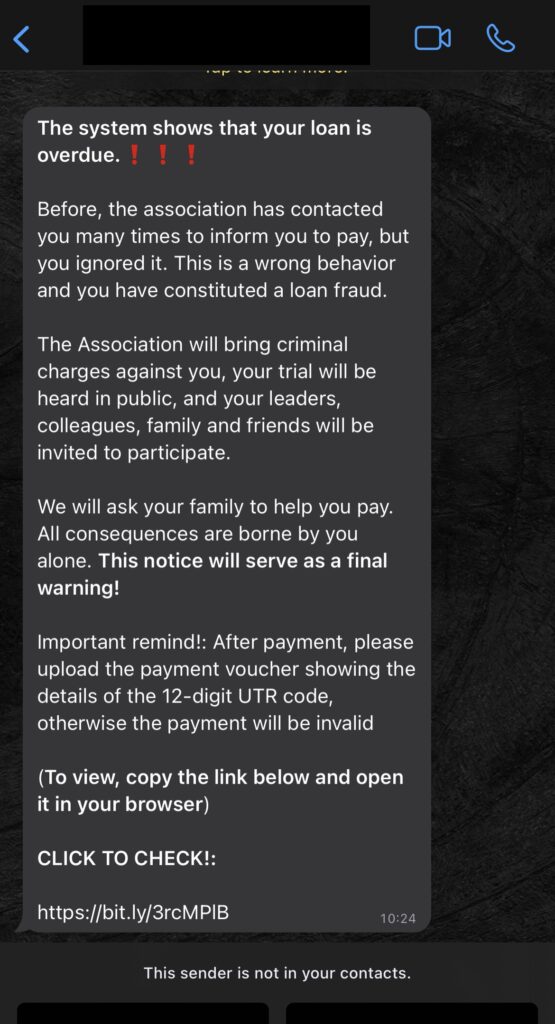
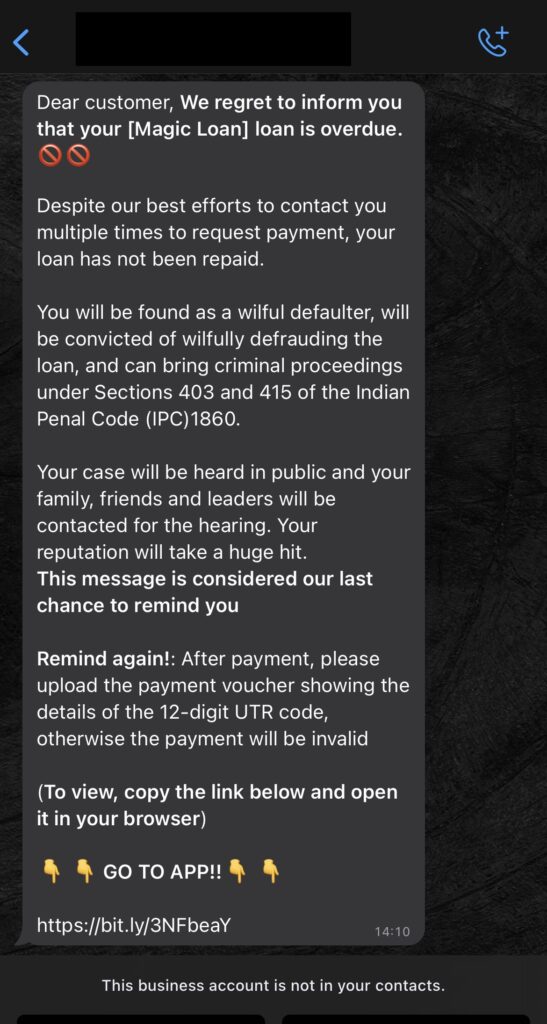
If users become suspicious and check the app’s comment section, they may realize their mistake. However, it is often too late, as scammers have already gained access to their personal data. The next day, victims receive alarming messages, claiming overdue loans, and threatening serious consequences for non-payment.
Step 6: Untraceable WhatsApp Messages:
Scammers prefer WhatsApp messages over calls due to their untraceable nature. They employ tools to generate random contact numbers and send messages to victims from those numbers. The messages often include sections from the Indian Penal Code (IPC), further intimidating victims into compliance.
The Payment Process and Coercion Tactics:
To extract payments, scammers employ a cunning strategy. Victims who download the app are presented with a screen displaying a UPI ID, an amount, and a field to enter the UTR reference number once payment is made. The UPI ID frequently refreshes to evade suspicion. However, these UPI IDs do not belong to the scammers; instead, they are rented out to fraudsters who withdraw the transferred amounts from those accounts.

Refusing to comply with scammers’ demands can lead to further threats and harassment. They persistently send intimidating messages and may contact victims’ emergency contacts. Additionally, scammers can misuse victims’ images and contacts, causing reputational damage by posting pictures on social media or sending bulk WhatsApp messages to all contacts, accusing victims of fraud.
Safeguarding Your Data Privacy:
While tracking down and apprehending scammers proves challenging, we can protect ourselves by taking proactive measures. Here are some essential tips to safeguard your data privacy:
1. Exercise Caution While Downloading Apps:
Carefully evaluate apps before downloading them, even from reputable app stores. Look beyond ratings and consider user reviews and comments. Beware of apps that request unnecessary permissions or exhibit suspicious behaviour.
2. Read Data Privacy Policies:
Before providing any personal information, review the data privacy terms and conditions associated with the app. Ensure the app follows industry best practices and respects your rights as a data subject.
3. Verify Legitimacy:
Ensure that NBFCs lending money are listed on the RBI NBFC list. The Reserve Bank of India (RBI) maintains a comprehensive list that you can refer to for legitimate lending institutions.
4. Check Credit Score Validation:
Legitimate financial institutions typically assess credit scores as part of the loan approval process. Be cautious if an app does not perform this standard check, as it may indicate fraudulent intent.
5. Retain Control over Your Data:
Legitimate apps allow users to delete their personal data as part of their data subject rights. Verify that the app provides an option to delete your information when no longer needed.
Conclusion:
Protecting our data privacy is crucial in today’s digital landscape. By remaining vigilant, understanding scamming techniques, and implementing necessary precautions, we can reduce the risk of falling victim to fraudulent schemes. Take charge of your personal information, exercise caution when downloading apps, and spread awareness among your friends and family. Let’s prioritize data privacy and stay one step ahead of scammers to create a safer digital environment for all.




