Risk Management
A security professional uses knowledge, skills, and experience to examine an organization’s operational risk management, develop strategies to use risk data effectively, work cross-functionally within an organization and report actionable information and findings to the stakeholders concerned. Terms such as threats, vulnerabilities, and assets are familiar to most cybersecurity professionals.
· An asset is something in need of protection.
· A vulnerability is a gap or weakness in those protection efforts.
· A threat is something or someone that aims to exploit a vulnerability to thwart protection efforts.
Risk Identification
How do you identify risks? Do you walk down the street watching out for traffic and looking for puddles on the ground? Maybe you’ve noticed loose wires at your desk or water on the office floor. As security professionals, we will continue to dig deeper to discover possible problems that could jeopardize the organization’s assets.
Identifying cyber security risks is a recurring process of identifying different possible risks, characterizing them, and then estimating their potential for disrupting the organization.
As security professionals, we will have a thorough knowledge of the organization’s strategic, tactical and operational plans.
Things to remember about risk identification:
· Identify risk to communicate it.
· Employees at all levels of the organization are responsible for identifying risk.
· Identify risks protecting against them.
As security professionals, we will be involved in risk assessment at a system level. We would focus on process, control, monitoring, incident response, and recovery activities. If we’re working with a smaller organization that lacks a risk management and mitigation plan and program, we might have the opportunity to help fill that planning void.
Risk Assessment
Risk assessment is the process of identifying, estimating, and prioritizing risks to an organization’s operations, assets, individuals, and other organizations. Risk assessment should result in aligning (or associating) each identified risk with the goals, objectives, assets, or processes that the organization uses to achieve its goals.
A risk assessment identifies the risk of fire to a building, as well as ways to minimize it. Fire alarms are the lowest cost and can alert personnel to evacuate and reduce the risk of personal injury. Sprinkler systems won’t prevent a fire but can minimize the amount of damage done. A gas-based system may be the best solution to protect the systems, but it might be cost-prohibitive. A risk assessment prioritizes these items for management to determine the method of mitigation that best suits the assets being protected.
When risk assessments are being performed, they are often documented in a report or presentation given to management for their use in prioritizing the identified risk(s). In some cases, management may request that a more in-depth or detailed risk assessment be performed by internal or external resources.
Risk Treatment
Risk management is the process of identifying, evaluating, and controlling risks. Decisions about risk depend on management’s attitude toward risk, its availability, and its cost. The options commonly used to respond to risk are:
Risk Mitigation
Risk mitigation is the most common type of risk management, and it involves taking steps to prevent or reduce the possibility of a risk event or its impact. Risk mitigation often involves establishing controls, such as security controls, to minimize adverse risks. Although risk cannot always be mitigated, measures such as safety measures should always be in place.

Risk Avoidance
Risk avoidance is a decision to eliminate risk exposure. This can mean ceasing operation for some or all of the activities of an organization that are exposed to the risk, or it could mean taking steps to minimize those risks. An organization may choose risk avoidance when the potential impact of a given risk is too high, or if the likelihood of that risk being realized is simply too great.
Risk Acceptance
Risk acceptance refers to management’s decision not to reduce the likelihood of a risk occurring by implementing a specific action. Management may opt for conducting the business function that is associated with the risk without any further action on the part of the organization, either because the impact or likelihood of occurrence is negligible, or because the benefit is more than enough to offset that risk.
Risk Transfer
Risk transference is the practice of transferring the risk of loss to another party in exchange for payment. Typically, this is an insurance policy.
Risk Priorities
After risks have been identified, it’s necessary to prioritize and analyze them using qualitative and quantitative analysis. This helps determine the root cause and narrow down apparent risks and core risks. Security professionals work with their teams to conduct qualitative and quantitative analyses.
Understanding the organization’s mission and the functions that support it helps set risks in context. This understanding helps determine the root causes of risks, prioritize their assessment and analysis, and determine a prioritized set of risk-response actions. Management usually provides direction for using the risk assessment findings to determine a prioritized set of risk-response actions.
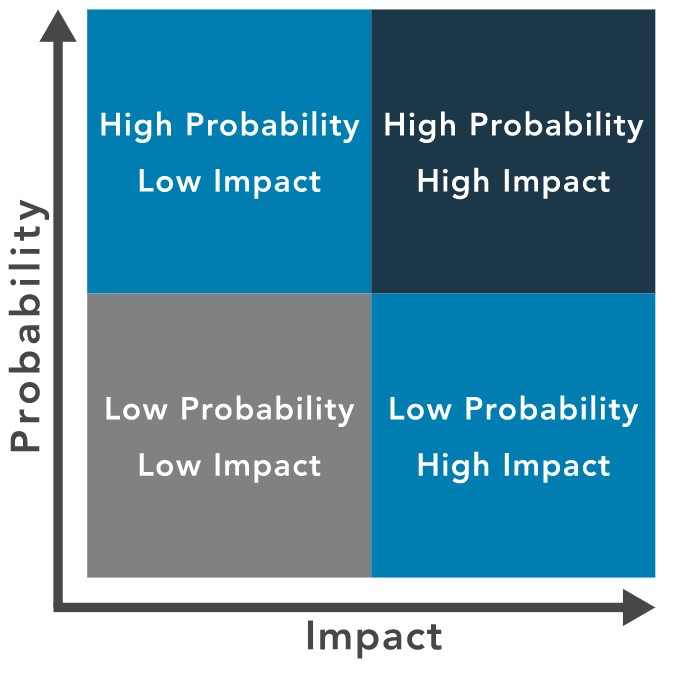
The risk matrix is a common method of prioritizing risks by identifying the intersection of the likelihood of occurrence and impact. This helps team members communicate with management when determining the final priorities. For example, a low likelihood and low impact might result in a low priority, while an incident with high likelihood and high impact will result in a high priority. Assignment of priority may relate to business priorities, the cost of mitigating risk, or the potential for loss if an incident occurs.
Decision-Making Based on Risk Priorities
When prioritizing risk, organizations must evaluate the likelihood and impact of risk as well as their tolerance for different sorts of risk. For example, a company in Hawaii may be more concerned about the risk of volcanic eruptions than a company in Chicago, but the Chicago company will have to plan for blizzards. In those cases, determining risk tolerance is up to management and directors. If a company chooses to ignore or accept the risk, of exposing workers to asbestos, say, it puts itself in a position of tremendous liability.




