The Largest DDoS Attack Ever Recorded By Google Recorded At 46 Million Requests Per Second
It is reported that Google was the target of the largest DDoS attack in history against one of its customers. On June 1st, a Google Cloud Armor client was attacked, sending 46 million requests per second through HTTPS DDoS attacks on a Google Cloud Armor client.
It is the strongest Layer 7 DDoS attack reported to date, breaking the previous record by at least 76%.
It would be tantamount to getting all daily queries to Wikipedia in just a few seconds, so you can get an idea of the scale of the attack.

By detecting and analyzing traffic early in the attack cycle, Cloud Armor Adaptive Protection prevented the attack from succeeding.
Cloud Armor recommended a client protection rule that was delivered to the client before the attack reached its maximum extent.
With the help of Cloud Armor, the customer’s service remained online, and its end users could continue to receive services.
Long-lasting Attack
The incident occurred at 09:45 am PT on June 1 and is believed to be a web-based attack. Attempting to compromise the victim’s HTTP/S load balancer, the attacker was initially only able to generate, 10,000 requests per second.
There was an increase of 100,000 RPS within eight minutes of the attack beginning. Upon receiving specific data extracted from Google’s traffic analysis, Cloud Armor Protection generated an alert and a signature triggered based on the data.
As a result of the attack, there was a spike of 46 million requests per second two minutes later. Thanks to Cloud Armor’s recommendation, the customer had already implemented the rule to enable normal operation. In the 69 minutes that followed the start of the attack, the attack ended.
This alert contained a recommendation for a rule that can be used to block signatures with malicious intent.
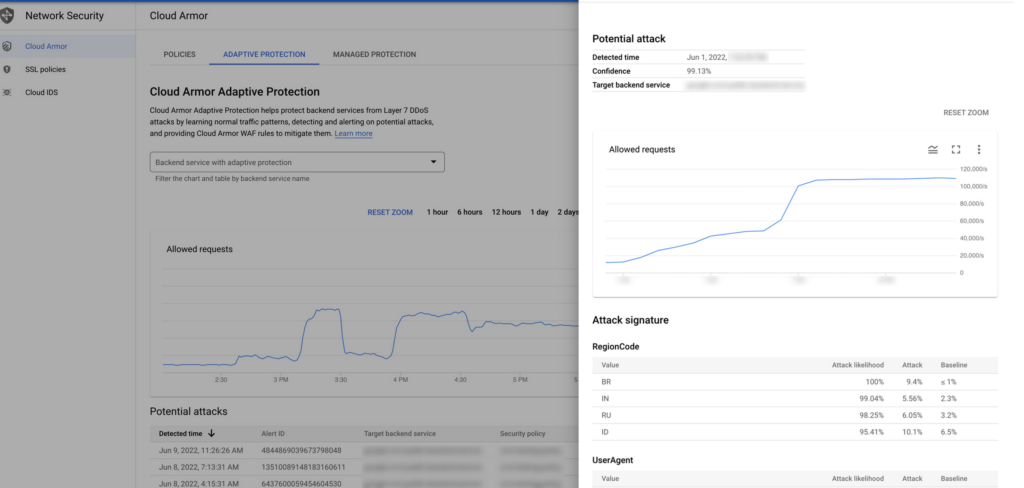
A total of 5,256 source IP addresses from 132 countries worldwide were involved in the attack. About 31% of all attack traffic was generated by the top 4 countries.
There is no information yet about the malware behind this attack. The Merit botnet seems to be the most likely provider of these services based on the geographic distribution of its usage.
The use of Tor egress nodes as the traffic delivery mechanism is another feature of this attack. According to Google researchers, a significant amount of unwanted traffic can be delivered through Tor exit nodes.
In addition, the size of the attack and the evolution of tactics will continue to increase in the coming years. Therefore, users should implement robust security mechanisms to ward off and mitigate such attacks.




