Understanding Vulnerability Assessment and Penetration Testing (VAPT): Techniques, Tools, and Best Practices
Vulnerability assessment and penetration testing (VAPT) are important techniques used to identify and evaluate the security of a computer system, network, or web application. These tests are typically performed by security professionals to identify #vulnerabilities that could be exploited by #attackers and to evaluate the effectiveness of existing security controls.
Vulnerability assessment is the process of identifying, analyzing, and reporting vulnerabilities in a system or network. This is typically done using automated tools that scan for known vulnerabilities and report on any that are found. These tools can scan for vulnerabilities in a wide range of systems, including operating systems, applications, and network devices.
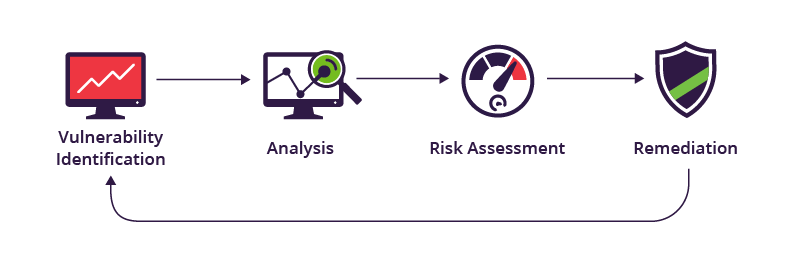
Penetration testing, on the other hand, is the process of actively trying to exploit vulnerabilities in a system or network. This is typically done by #security professionals who manually test systems and networks to identify and exploit vulnerabilities. The goal of penetration testing is to identify vulnerabilities that could be used by an attacker to gain #unauthorized access to a system or network.

There are many different tools and techniques that can be used for VAPT, including:
- Vulnerability #scanners: These are automated tools that scan for known vulnerabilities in a system or network. Examples include Nessus, OpenVAS, and Qualys.
- Web application scanners: These are specialized tools that are used to scan web applications for vulnerabilities. Examples include Burp Suite, #OWASP ZAP, and Acunetix.
- Manual testing: This involves manually testing systems and networks to identify vulnerabilities. This can include techniques such as #socialengineering, password cracking, and network sniffing.
When it comes to best practices for VAPT, there are a few key things to keep in mind:
- Regular testing: It’s important to regularly perform vulnerability assessments and penetration testing to ensure that any new vulnerabilities are identified and addressed in a timely manner.
- Keep software and systems up to date: Make sure to keep all software and systems up to date with the latest security #patches and #updates.
- Document and track vulnerabilities: It’s important to document and track all vulnerabilities that are identified during VAPT so that they can be properly prioritized and addressed.
- Train employees: Regularly train employees on security best practices and what to look out for when it comes to potential vulnerabilities.
In conclusion, Vulnerability Assessment and Penetration Testing (VAPT) is a crucial process that helps identify and evaluate the security of a computer system, network, or web application. These tests are typically performed by security professionals to identify vulnerabilities that could be exploited by attackers and to evaluate the effectiveness of existing security controls. Best practices for VAPT include regular testing, keeping software and systems up to date, documenting and tracking vulnerabilities, and training employees about security.




