Uber Hacked – Full Access Granted to Hacker
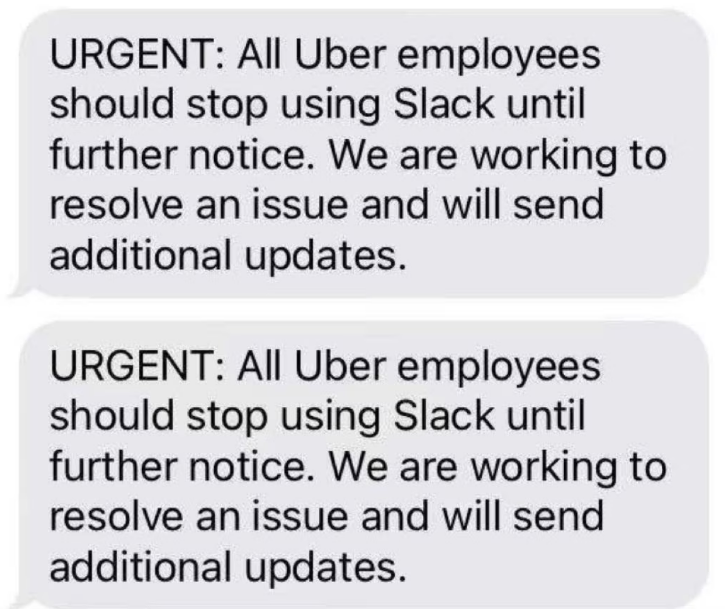
A breach in Uber’s computer network was discovered that caused several internal communication systems and engineering systems to be taken offline by the company.
It appears that there have been many internal systems at Uber that have been compromised by this breach. It has almost been confirmed that the hackers have accessed Uber to its full extent.
Cybersecurity researchers received images of emails, cloud storage services, and code repositories of Uber provided by a person declaring responsibility for the hack.
Hacked Uber Systems
Apart from the critical Uber IT systems, the hackers managed to gain access to other crucial Uber systems. And here below we have mentioned them: –
- Amazon Web Services console
- VMware ESXi virtual machines
- Google Workspace email admin dashboard
- Slack server
It has been confirmed by Uber that the attack took place and they have tweeted that they are in contact with the law enforcement agencies. Also, they confirmed that additional information will be posted soon once they have it.

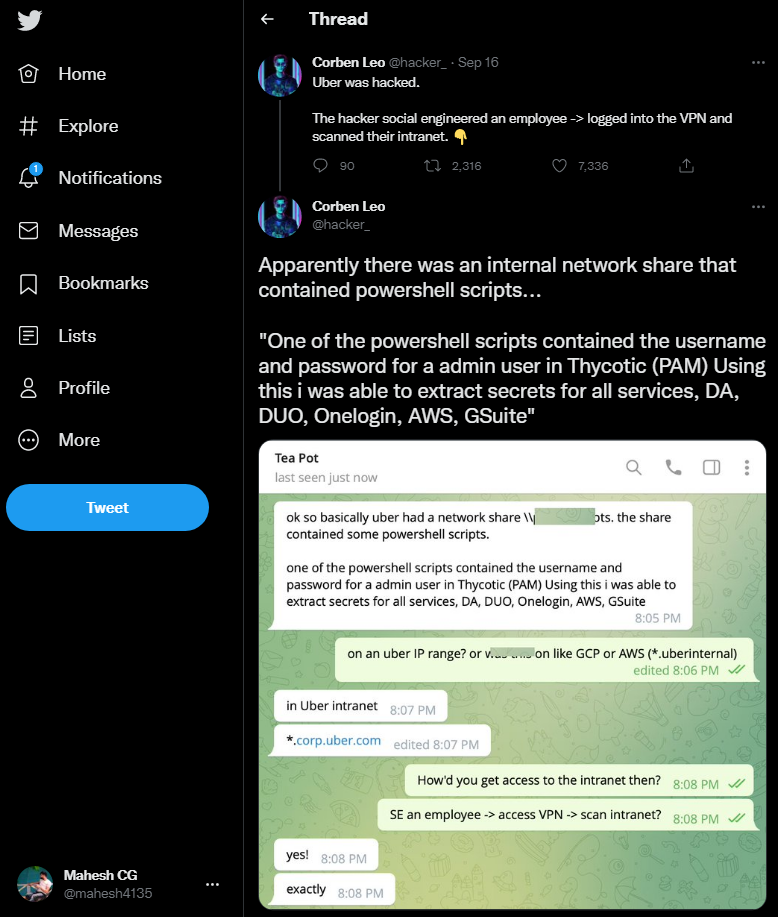
After a social engineering attack against an Uber employee and stealing the password of that employee, the threat actor claimed they had breached the company.
The threat actor was able to gain access to the company’s internal systems after stealing the credentials of the company’s internal systems.
Hacker One Flaw
During this attack, the threat actor may have stolen Uber’s data and source code, but there is no way to confirm this. Furthermore, they had access to an asset that had the potential to be even more valuable than they already were.

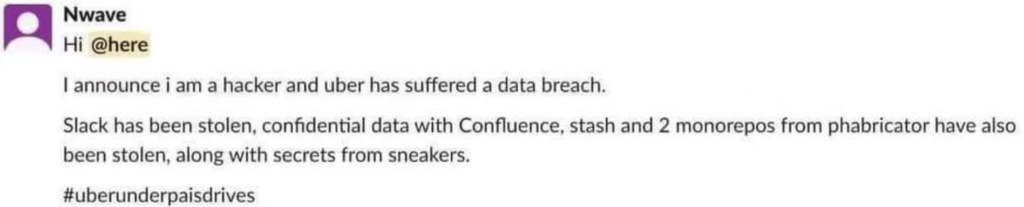
Here’s what the Yuga Labs security engineer Sam Curry stated: –
“It’s possible that the threat actor may also have access to the Hacker One bug bounty reward program of Uber. On this page, they have commented on all bug bounty tickets submitted by the company.”
Through this program, cybersecurity experts secretly find and report all the flaws affecting systems and apps of Uber. So, all the reports of these flaws were kept confidential by the company itself until they were fixed.
All of the company’s private vulnerabilities submitted through the Hacker One program by the experts were accessible to the threat actor.
Before losing access to Uber’s bug bounty program, the attacker downloaded all of Uber’s vulnerability reports. So, to prevent further access to the vulnerabilities disclosed secretly, Uber has disabled the Hacker One program for now.
While apart from this, it was reported that Uber’s top security executive at the time, Joe Sullivan, had resigned from his position because of his role in responding to the hack.




